2017–23 Integrated Risk based Internal Audit and Evaluation Plan
Updated February 2021
Table of Contents
- Executive Summary
- Planning Context
- Planning Approach
- Key Audit and Evaluation Requirements
- Evaluation Coverage and Plan
- Internal Audit Plan
- Planning Approach
- Identification of the Audit and Evaluation Universe.
- Environmental Scan
- Prioritization of Audit and Evaluation Entities
- Risks Identified during the Risk Environmental Scan
- Project Selection and Plan Development
- Audit and Evaluation Plan and Summary
- Detailed Audit and Evaluation Plan (2017–23)
- Appendix A: OIC Key Organizational Risks Identified for 2014–18
- Appendix B: OCG Prioritization of the Audit Universe – Small Department Risks
- Appendix C: OIC Interview Results and Risk Evaluation
- Appendix D: OIC Risk Heat Map
- Appendix E: Organization Chart
Executive Summary
Introduction
This document presents the Risk-Based Audit and Evaluation Plan (RBAEP) for the Office of the Information Commissioner of Canada (OIC), updated February 2021. The RBAEP combines both the internal audit plan and the evaluation plan up to the end of 2022–23. The objective of the RBAEP is to allocate resources to the areas of most significant risk and priority to the OIC, as well as to align with the requirements of Treasury Board (TB) policies on Results and Internal Audit.
The RBAEP builds on the OIC’s 2014–18 Risk-Based Audit and Evaluation Plan and the Office of Comptroller General’s Three-year Risk-based Internal Audit Plan for 2016-17 to 2018–19 and through the integration of evaluation projects in accordance with the TB Policy on Results and Internal Audit. The plan identifies resource requirements to ensure that requests from the Audit and Evaluation Committee and the Executive Committee can be allocated efficiently and in a timely manner. The RBAEP reconfirms the objective of allocating resources to those areas that are of the most significant organizational priority and to ensure that internal audit and evaluation services provide the greatest benefit to the OIC.
As an Agent of Parliament, the OIC reports directly to Parliament and is excluded from the traditional oversight by the Treasury Board of Canada Secretariat (TBS). However, the OIC must have an audit and evaluation committee in place and considers its internal oversight mechanisms and governance structure to be of the utmost importance in helping ensure that adequate management practices are in place.
Proposed Audits and Evaluations
| Year | Audit Project Name | Primary OIC Entity |
|---|---|---|
| 2017–18 | Threat Risk Assessment (TRA) and Threat Vulnerability Assessment (TVA) – narrow scope | Information Technology (IT) |
| 2018–19 | Audit of Contracting and Procurement | Canadian Human Rights Commission (CHRC) and OIC - Finance |
| 2018–19, 2019–20 and 2020–21 | Threat Risk Assessment (TRA) and Threat Vulnerability Assessment (TVA) – wide scope | Information Technology (IT) |
| 2021–22 and 2022–23 | Evaluation of Investigations | Senior Management and Complaints Resolution |
| 2021–22 | Performance and Talent Management Review | Human Resources (HR) |
| 2022–23 | Audit of Information Management and Physical Security | Corporate Services |
Planning Context
Background
The Information Commissioner is an Agent of Parliament appointed under the Access to Information Act.
The Commissioner reviews complaints about how federal organizations apply to Act, so Canadians can receive the information to which they are entitled. The Commissioner is the first level of independent review of government decisions relating to requests for access to public sector information. The Act requires the Commissioner to investigate all the complaints she receives. The Office of the Information Commissioner (OIC) supports her in her work.
The OIC is to conduct efficient and fair investigations, be open and transparent when dealing with institutions and complainants, and provide expert advice to Parliament and other stakeholders on access to information.
The OIC also supports the Commissioner in her advisory role to Parliament and parliamentary committees on all matters pertaining to access to information. The OIC actively makes the case for greater freedom of information in Canada through targeted initiatives such as Right to Know Week and ongoing dialogue with Canadians, Parliament and institutions.
Caroline Maynard was appointed to the position of Information Commissioner of Canada for a seven-year term on March 1, 2018.
Amendments to the Access to Information Act
The OIC received permanent funding in August 2019 to operationalize the new powers and responsibilities the Commissioner received under Bill C-58. These powers, which include order making and publishing, and responsibilities such as ruling on applications from institutions to decline to act on an access request.
Government-Wide Priorities
In the Mandate Letter to the President of the Treasury Board, the following priority is stated: “Work with the Minister of Justice to enhance the openness of government, including leading a review of the Access to Information Act to ensure that Canadians have easier access to their own personal information, that the Information Commissioner is empowered to order government information to be released and that the Act applies appropriately to the Prime Minister’s and Ministers’ Offices, as well as administrative institutions that support Parliament and the courts.”
Similar priorities were also stated in the Mandate Letters to the Minister of Justice and Attorney General of Canada, and the Minister of Democratic Institutions.
The Government of Canada is currently one of four supporting Open Government Partnership co-chairs. In 2018–19, it will be the lead government co-chair.
A commitment to an open and transparent government relates directly to the mandate of the OIC.
OIC Strategic Priorities
We will pursue three strategies to achieve our vision, deliver our mission and live out our values:
-
Invest in and support our resources: Our work is challenging and labour-intensive, and requires dedicated, professional staff to carry out. Our team of more than 100 investigators, lawyers, communicators, ATIP specialists, and IM/IT, human resources, finance, security and accommodations experts works together to support the Information Commissioner and deliver her mandate under the Access to Information Act.
-
Innovate and transform our operations: The revolution in technology, the unrelenting interest of Canadians in holding government to account and the reality of the 24-hour news cycle mean we cannot be complacent about how we do our work. Being innovative and transforming our operations—through the creative use of technology, smart and efficient processes, and targeted expertise—will position us to be more agile and responsive in the face of challenges, serve complainants better and help us meet our corporate obligations.
-
Maintain and enhance our reputation: Our credibility depends on our putting our words into action and being an example for institutions through the timeliness and quality of our work. Stakeholders—ranging from ordinary citizens to access to information specialists to parliamentarians—look to us for well-researched facts and opinions on access and transparency.
These priorities were taken into consideration when finalizing the RBAEP.
OIC Structure and Resources
Workforce and Organizational Structure: The OIC’s workforce comprises 135 approved full-time equivalents (FTEs). Of the 135 FTEs, 103 are for the core responsibility and the other 32 for Internal Services. Please see Appendix E for the organization chart.
Financial Resources:The OIC’s overall Main Estimates for the last five years ranged from $11,291,086 in 2016-17 to $13,068,088 in 2020–21.
Complaints History: The OIC receives two types of complaints: administrative and refusal. Any complaint not resolved during the fiscal year it is received is carried over to the following year and now considered a part of the inventory of complaints. The following graph outlines the number of cases received, resolved and carried over since 2014–15.
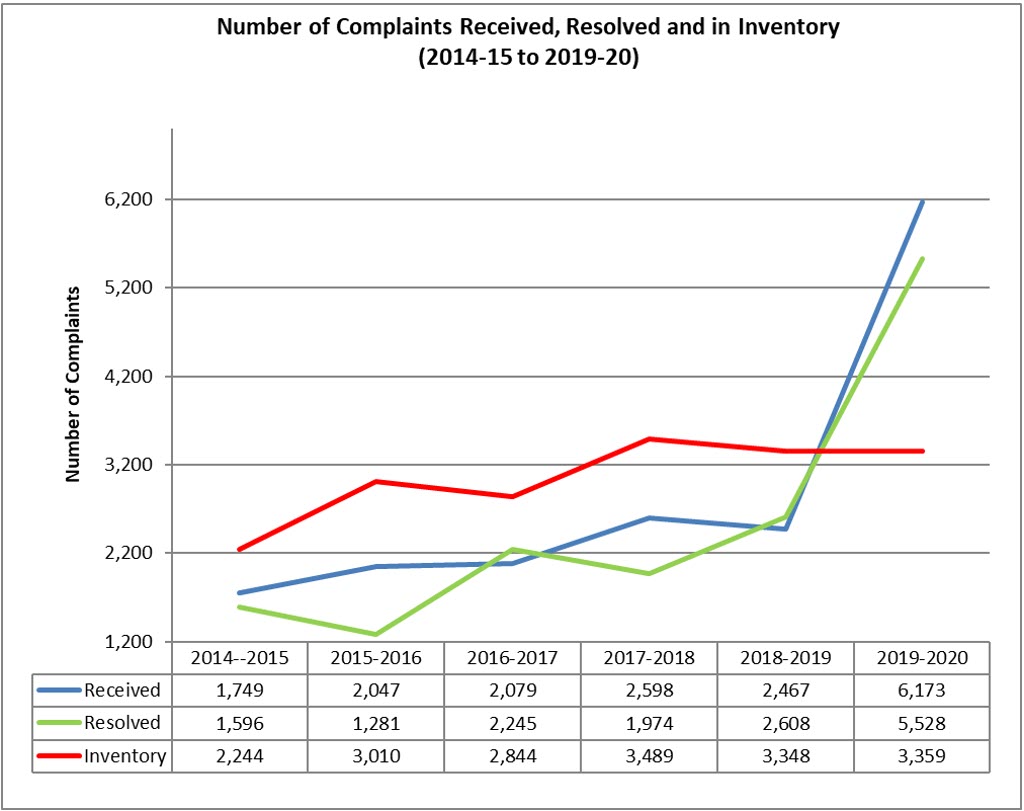
Text version
The figure is a line graph showing the number of complaints the Commissioner registered, resolved as well as the unresolved complaints that remained in the inventory at the end of the year. The figure demonstrates the totals from 2014–15 to 2019–.
In 2014–15, the Commissioner received 1,749 complaints, resolved 1,596 complaints and 2,244 unresolved complaints remained in inventory at the end of the year.
In 2015-2016, the Commissioner received 2,047 complaints, resolved 1,281 complaints and 3,010 unresolved complaints remained in inventory at the end of the year.
In 2016-2017, the Commissioner received 2,079 complaints, resolved 2,245 complaints and 2,844 unresolved complaints remained in inventory at the end of the year.
In 2017–18, the Commissioner received 2,589 complaints, resolved 1,974 complaints and 3,489 unresolved complaints remained in inventory at the end of the year.
In 2018–19, the Commissioner received 2,467 complaints, resolved 2,608 complaints and 3,348 unresolved complaints remained in inventory at the end of the year.
In 2019–20, the Commissioner received 6,173 complaints, resolved 5,528 complaints and 3,359 unresolved complaints remained in inventory at the end of the year.
Progress on Implementation of the 2014–18 OIC Audit and Evaluation Plan
An Audit and Evaluation Plan was completed in 2013 that listed the following audit and evaluation projects for completion by the end of March 2018. The progress made on this Plan has been factored into this new Plan. The chart below summarizes the status of the 2014–18 Plan:
| Year | Audit Project Name | Primary Entity | Current Status |
|---|---|---|---|
| 2013–14 | Audit of Staffing and Governance | Corporate Services | Completed March 2013 (Samson) |
| 2014–15 (post- move) | Audit of Information Technology and Physical Infrastructure Security | Corporate Services | Completed September 2016 (Samson) TRA/TVA On-going (Cistel) |
| 2014–15 | Evaluation of Complaints Resolution and Investigations, Phase I: Development of Performance Measurement and Evaluation Framework | Complaints Resolution and Compliance | Performance measurements have been developed to track median turnaround times to resolve complaints, as well as tracking the number of recommendations implemented. |
| 2015–16 | Audit of Procurement and Contracting | Corporate Services | Completed in 2018–19 (Samson) |
| 2015–16 | Audit of Information Management | Corporate Services | Completed September 2016 (Samson) April 2017 (RHEA) |
| 2016–17 | Evaluation of Investigations, Phase II: Implementation | Complaints Resolution and Compliance | Pending |
| 2017–18 | Audit of Case Management System | Corporate Services | Pending |
OIC Key Organizational Risks (2013-14)
The following list of key organizational risks was developed in 2012. At that time, the OIC was going through a significant transition as it was physically moving its office space to the current location at 30 Victoria. At the same time, the government was facing a workforce adjustment period that led to a reduction of 5% in appropriated funding levels. These risks were reviewed and considered in the development of an up to date OIC risk profile:
- Financial resource constraints
- Changing complaints picture
- Workforce
- Change management
- Physical and information technology (IT) security
- Inadequate performance measures and targets
OCG Risk Prioritization for Small Department Risks
Treasury Board Secretariat (TBS) provides central audit and oversight through a Small Departments and Agencies (SDA) audit committee with externally appointed members to oversee 42 small government departments and 5 regional development agencies with fewer than 500 employees and $300 million in annual approved expenditure. While the OIC, as an independent Agent of Parliament, is not subject to this oversight, it does, nonetheless, choose to consider the SDA high risk categories that TB has established in its audit plan priorities. TBS has identified nine areas for audit consideration:
- Information Technology Management
- Compensation
- Management of Shared and Common Services
- Workforce Management
- Security Management
- Contracting and Procurement
- Regulatory Management
- Management and Oversight (Financial and non-financial information for decision making)
- Investment Planning and Project Management
Please see Appendix B for further information regarding the risk profile for SDAs as of October 2016.
Planning Approach
Key Audit and Evaluation Requirements
There are a number of TB policies, directives and guidelines that establish the requirements and best practices for audit and evaluation planning in the federal government. These policies, directives and guidelines were used as best practices in the development of the RBAEP. This section highlights some of the key requirements and obligations and presents the approach used to assess and prioritize projects for inclusion in the RBAEP.
Evaluation Coverage and Plan
For Government of Canada, evaluation is the systematic collection and analysis of evidence on the outcomes of programs in order to make judgments about the value for money of federal government programs and alternative ways to deliver them to achieve the same results.
In accordance with TB policy, federal institutions are required to prepare a rolling five-year evaluation plan. The plan’s required coverage is twofold:
The Financial Administration Act (section 42.1) requires that an evaluation be performed of all ongoing grant and contribution programs on a five-year cycle (does not apply to the OIC).
The TB Policy on Results requires that, starting in 2016, Deputy Heads are responsible for annually approving and providing to the Treasury Board of Canada Secretariat, in the manner and timing prescribed by the Secretariat, an evaluation plan that clearly presents planned evaluation coverage, including coverage of organizational spending and the programs in the Program Inventory, during the planning period. The Policy on Results exempts Agents of Parliament from having to provide a five-year audit and evaluation plan.
In addition, there are a number of other potential planning requirements. Notably, evaluation plans must also do the following:
- align with the Departmental Results Framework (DRF);
- support the Expenditure Management System;
- include the administrative aspect of major statutory spending (does not apply to the OIC); and
- include other programs, specific evaluations or elements of the government’s overall evaluation plan, when applicable.
Given the OIC’s mandate, direct program spending is limited to one program area: compliance with access to information obligations. The internal services program supports this program. While the OIC does not have an internal evaluation function, a formal performance measurement strategy is in place and the annual report provides detailed and comparative analysis of OIC’s performance of both its program area and internal services. More in-depth reviews are undertaken, when warranted, to assess underlying causes of emerging trends and variations in performance in safeguarding access to information rights under the Act.
Internal Audit Plan
Internal audits provide independent, objective and substantiated conclusions on the effectiveness of risk management, control and governance processes. The focus is on all management systems, processes and practices, including the integrity of financial and non-financial information. Internal audit assurance services provide evidence-based opinions on the extent to which the system of internal controls is adequate and effective to support the following imperatives:
- achievement of operational objectives;
- safeguarding of assets;
- economy and efficiency of operations;
- reliability and integrity of financial and operational information; and
- compliance with legislation, policies and procedures
In accordance with TB policy, internal audit plans must ensure coverage of areas of higher risk and significance. The internal audit plan should also have the following characteristics:
- be risk-based;
- be reviewed by the audit committee;
- be focused predominantly on the provision of assurance services;
- have a multi-year horizon;
- address risks and internal audits identified by the Comptroller General as part of government-wide coverage; and
- support annual assurance reporting on the overall state of organizational risk management, control and governance processes
Planning Approach
The approach on which this plan is based complies with the Institute of Internal Auditors’ International Professional Practices Framework. The RBAEP was developed using the approach outlined in the following figure.
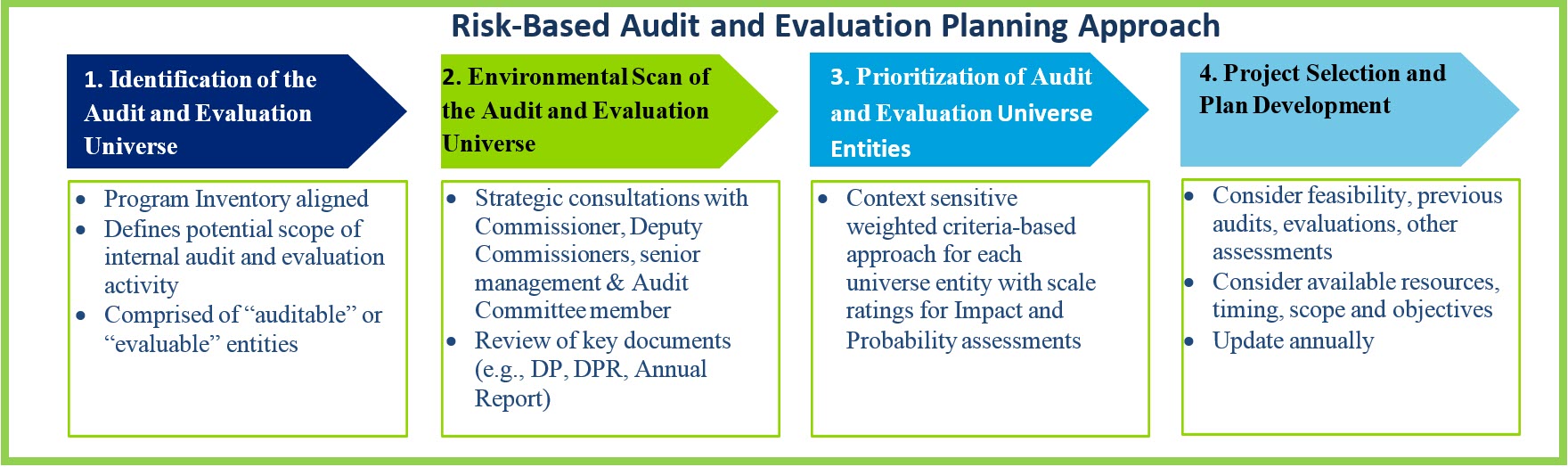
Text version
This graphic shows the planning approach of the risk-based audit and evaluation plan. There are four main steps to the planning approach that are displayed in separate boxes in order from right to left. The boxes are shaped as arrows that point to the right and contain the title of each planning step. Below each arrow-shaped box are bullets providing more details for each step.
Step 1: Identification of the Audit and Evaluation Universe
Additional information:
- Program Inventory aligned
- Defines potential scope of internal audit and evaluation activity
- Comprised of “auditable” or “evaluable” entities
Step 2: Environmental Scan of the Audit and Evaluation Universe
Additional information:
- Strategic consultations with Commissioner, Deputy Commissioners, senior management & Audit Committee member
- Review of key documents (e.g., DP, DPR, Annual Report)
Step 3: Prioritization of Audit and Evaluation Universe Entities
Additional information:
- Context sensitive weighted criteria-based approach for each universe entity with scale ratings for Impact and Probability assessments
Step 4: Project Selection and Plan Development
Additional information:
- Consider feasibility, previous audits, evaluations, other assessments
- Consider available resources, timing, scope and objectives
- Update annually
Identification of the Audit and Evaluation Universe
The audit and evaluation universe defines the potential scope of proposed engagements and comprises individual “universe entities” that may be the subject of internal audit or evaluation activity. To ensure alignment between the focus of internal audit and evaluation projects with the OIC’s operational structure, the universe entities were aligned with the OIC’s program and internal services, as identified in the Program Inventory (PI).
The following table presents the OIC’s audit and evaluation universe:
| Audit and Evaluation Universe | |||
|---|---|---|---|
| Strategic Outcome | A transparent, accountable and responsive federal government | ||
| Program | 1. Compliance with access to information obligations | ||
| Audit and Evaluation Universe Entities | Investigations (three organizational units) | ||
| Litigation | |||
| Advice to Parliament | |||
| Program | 2. Internal services | ||
| Audit and Evaluation Universe Entities | Commissioner’s Office | Corporate planning and reporting | Human resources management |
| Finance | Information technology | Information management | |
| Access to information and privacy | Procurement, acquisition cards and contracting | Travel and hospitality | |
| Values and ethics | Administrative services | Internal audit and evaluation |
Environmental Scan
A series of interviews were conducted with the Information Commissioner, the Deputy Commissioners, management and an external member of the Audit and Evaluation Committee to identify organizational changes, key risks to which operations are exposed, and areas in which internal audit or evaluation could provide the most value in supporting the achievement of organizational objectives. It should be noted that the interviews were conducted shortly after the government announced the legislative changes to the Act and current Information Commissioner announced she would not seek another term. These announcements were reflected in the risks identified in the interviews.
Key documents, such as the 2016-17 Annual Report, 2016-17 Departmental Performance Report (DPR) and the 2017–18 Departmental Plan (DP), were reviewed to facilitate the identification of organizational priorities and key risk areas. This information not only provided important insight into areas of management focus but also risk exposure information that was used to identify the universe entities and to prioritize audit and evaluation projects. As a start point for the interviews, key risks as determined by the Office of the Comptroller General (OCG) were considered for risk ranking during the interviews as well as the key risks that were identified in 2013 for the RBAEP.
Prioritization of Audit and Evaluation Entities
During the course of the Management Interviews, each potential risk was ranked using two criteria: risk probability of occurrence and risk impact on the OIC on scales of 1 (low) to 5 (high). Final ranking results can be found in Appendix C.
Both scores for each risk were averaged out in order to prioritize risk areas to OIC. Furthermore, the risks were then plotted on an X and Y access to visualize which had the highest impact and probability. This heat map can be found in Appendix D.
Risks Identified during the Risk Environmental Scan
During the environmental scan, the following risks were identified as the most probable and having the greatest impact on the OIC. Some or all aspects of these risks are outside the OIC’s control.
Changes to the Access to Information Act: The tabled legislative changes to the Act could have an impact on the number of complaints received by the OIC and the operating environment in which it conducts its investigations. The passage of the Bill has been slower than expected and the coming-into-force date is not known. Indeed, it is not clear whether the Bill will be passed prior to the October 2019 election.
Human resources: As an Agent of Parliament, the risk of having an insufficient number of employees with the breadth and depth of experience necessary to complete activities or address competing priorities is constant. Furthermore, the loss of qualified employees to larger organizations with more opportunities for advancement could have an impact on the OIC’s ability to deliver its mandate in a timely manner.
Contracting and procurement: The OIC has an agreement in place authorizing the Canadian Human Rights Commission (CHRC) to provide procurement and contracting services. The contracting out of this service (reliance on another organization), compliance with contracting policies and regulations, employee turnover at CHRC, urgency of investigator contracts and the potential impact on service levels, have been identified as potential risks to the OIC.
Information Technology and Management: The impact of a security breach leading to the divulging of any information obtained during an investigation, including personal and/or top secret information, could have a very significant impact on the reputation of the OIC and its ability to meet its legal obligation to safeguard the information rights. As the OIC continues to move more aspects of its complaint receipt and investigation activities electronically, this risk remains prevalent.
Phoenix Pay Issues: While the OIC has fared better than other federal organizations in terms of Phoenix pay issues, continuing to respond promptly to those do arise is crucial. Not doing so puts employee welfare at risk and could also affect morale, recruitment and productivity.
Other notable risks include the ongoing increase in access requests (more than 100,000 in 2017–18) and the possibility that the OIC will receive complaints as a result. Decreasing institutional performance, which may also lead to more complaints. In addition, the OIC continues to operate with inadequate permanent funding to handle the level of complaints and meet mandate requirements. Finally, the cultural shift to a more open and transparent government continues to be slow.
Project Selection and Plan Development
Audit and evaluation projects were selected to be included in the OIC RBAEP with the highest audit priorities identified serving as the starting point and providing the main but not only consideration for project selection. The top priority risks topics were examined against a variety of constraints and opportunities, including the following:
- recently completed audits
- availability of audit and evaluation resources over the three-year period;
- feasibility of conducting an audit or evaluation;
- other reviews providing oversight (i.e. evaluations, Office of the Auditor General (OAG) audits);
- mandated audit projects (i.e. follow-ups, OAG, Office of the Comptroller General and Public Service Commission obligations for horizontal audits);
- risk tolerance;
- management requests; and
- Audit and Evaluation Committee and senior management direction.
In finalizing the RBAEP, care was taken to ensure the audit and evaluation universe was appropriately covered. The RBAEP reinforces the integration of audit and evaluation projects, when feasible, while ensuring evaluation coverage of all direct program spending.
Audit and Evaluation Plan and Summary
The audit and evaluation coverage proposed in the RBAEP strives to achieve an effective balance between a number of requirements and considerations and allows for carrying out one or two projects per year. The three-year Plan takes into account the necessary alignment with organizational risks and priorities.
The OIC has one program, namely “Compliance with access to information obligations”. The TB Policies on Results requires that, starting in April 2017, "Deputy Heads for Agents of Parliament are responsible for annually approving and providing a departmental evaluation plan to the Treasury Board of Canada Secretariat, in the manner and timing prescribed by the Secretariat, that clearly present planned evaluation coverage, including coverage of organizational spending and the programs in the Program Inventory, during the planning period." An evaluation of Investigations was recommended in 2013 and this carries over to the current RBAEP for the aforementioned reason.
This RBAEP is based on a fundamental assumption regarding allocated funding. While there is an annual budget, it will be subject to change due to any rescheduling or based on actual costs of the audit or evaluation
It is expected that the OIC will achieve coverage of its highest audit and evaluation priorities over the four-year planning horizon. When the feasibility or value of either conducting or continuing an audit or evaluation project is in question—due to factors such as new priorities, or lack of resources or subject-matter expertise—the Chief Audit Executive will bring this to the attention of the Audit and Evaluation Committee for consideration and approval.
Detailed Audit and Evaluation Plan (2017–23)
The table below provides the scope, objective and rationale for each of the audit and evaluation projects proposed for 2017–18 to 2022–23. The rationale includes, where applicable, a mapping to the identified key risks facing the OIC and a reference to the audit priority rating detailed in Appendix D. It should be noted that final scope, objectives and estimated budgets for the proposed audits/evaluations may be modified depending on the results of the planning phases of each of the respective projects. In addition to the audit projects below, internal auditors will continue to attend key management and Audit and Evaluation Committee meetings, conduct follow-ups on previous audits (as appropriate), and develop the engagement scope for projects identified in the RBAEP.
| Year | Audit Project Name | Primary Entity | Audit Scope, Objective and Rationale |
|---|---|---|---|
| 2017–18 | Treat Risk Assessment (TRA) and Threat Vulnerability Assessment (TVA) – Narrow Scope | Information Technology (IT) | Scope: OIC network analysis and gather information Objective: To assess the level of vulnerability of the OIC network with relation to external threats i) conduct interviews of stakeholders and system owners at the OIC; ii) conduct penetration testing; and iii) provide a report and conduct an on-site debriefing. Rationale: High audit requirement, 4.1 Impact and 2.6 Probability. This audit is seen as essential as the OIC launches its online complaint form. The risk of disclosing confidential information, including personal information, is of greatest concern to the OIC. |
| 2018–19 | Audit of Procurement and Contracting | Canadian Human Rights Commission (CHRC) | Scope: Management practices and assessment of controls related to procurement and contracting at CHRC. Objective: Assess the operational efficiency, accuracy and compliance of procurement and contracting practices and processes as well as the extent to which procurement activities support business lines and organizational objectives. Rationale: High audit requirement, 3.3 Impact and 3.3 Probability. The OIC has reached an agreement to have its contracting and procurement services to CHRC. Considering the complexity and stringent policies around federal procurement and contracting policies, the inherent reputational risk associated with these activities, an audit of this activity is highly recommended. |
| 2018–19, 2019– and 2020–21 |
Treat Risk Assessment (TRA) and Threat Vulnerability Assessment (TVA) – Wide Scope | Information Technology (IT) | Scope: OIC network analysis and gather information Objective: To assess the level of vulnerability of the OIC network with relation to external threats i) conduct interviews of stakeholders and system owners at the OIC; ii) conduct penetration testing; and iii) provide a report and conduct an on-site debriefing. Rationale: High audit requirement, 4.1 Impact and 2.6 Probability. This audit is seen as essential as the OIC launches the document upload functionality for the online complaint form. |
| 2021–22 and 2022–23 |
Evaluation of Investigations | Complaints Resolution and Compliance | Scope: The Investigations program. Objective: Address, as per the TB Policy on Results, the relevance and performance of the investigations program. The evaluation should consider the evolving nature of investigations through an analysis of the portfolio of complaints (e.g. source, targeted institution, complaint type), as well as the new context in which the program is operating (e.g. C-58 legislative changes). Rationale: High evaluation requirement, 4.2 Impact and 3.6 Probability. Given unprecedented circumstances of covid-19, the OIC has experienced procurement delays however there may be an opportunity to develop/improve plans to ensure both a smooth transition and an adoption of more efficient processes. Therefore, an evaluation rescheduled to 2021–22 and 2022–23 would be more beneficial and valuable, as it will produce better results. Considering that, the Investigations program is the key program at the OIC, an evaluation of this activity is recommended every 5 years. |
| 2021–22 | Performance and Talent Management Review | Human Resources (HR) | Scope: A review of OIC HR practices Objective: Not an in-depth audit, but a review of the following OIC HR practices i) effectiveness of employee performance evaluation; ii) effectiveness of Talent Management program, iii) employee turnover, and iv) exit interviews. Rationale: High audit requirement, 3.3 Impact and 3.4 Probability. During the interviews of Management and the Strategic Planning meeting, the need to recruit high performing employees in several key positions was identified as a high priority. Given unprecedented circumstances of covid-19, there may be an opportunity to develop/improve plans to ensure both a smooth transition and an adoption of more efficient processes. A review postponed to 2021–22 would be more beneficial and valuable, as it will produce better results. |
| 2022–23 | Audit of Information Management and Physical Security | Corporate Services | Scope: Management practices and assessment of controls related to information management. Objective: Assess the operational effectiveness of information management practices and compliance with recommendations made in the RHEA audit, notably as they relate to the retention and disposition of sensitive and restricted documents. Rationale: High audit requirement, 3.2 Impact and 2.3 Probability. Considering the sensitivity of the information retained by the OIC, and the reputational risk to the OIC in the case of improper management of private or restricted information, an audit of this activity is highly recommended but for 2022–23 instead of 2021–22. This change is due to the pandemic situation and the derogation in effect in the IM Security. |
Appendix A: OIC Key Organizational Risks Identified for 2014–18
| Rank | Auditable Entry | Risks Identified | Relevance in 2017 |
|---|---|---|---|
| 1 | Financial resource constraints | The risk that successive and significant budget cuts have placed the OIC at the limit of its financial and organizational flexibility. | The OIC still lacks sufficient funds to meet its mandate. |
| 2 | Changing complaints picture | The risk that continued significant increases in complaints received could seriously stretch OIC’s investigative resources, possibly resulting in a growing inventory of complaints. A further risk is that institutions may not be able to respond to investigative queries in a timely manner, which could result in the OIC having to follow more formal processes, in increased litigation and, ultimately, in there being a negative impact on requestors’ rights. | The OIC still faces this challenge in 2017. In fact, the number of complaints has only risen since 2014, however resources have remained stagnant. Also, see relevance comments under # 4 below. |
| 3 | Workforce | The risk that the 2013–2014 office move will have a negative impact on OIC’s productivity. Productivity will be diminished during the move and there will be a period of diminished efficiency as the workforce adjusts to the new tools and space under Workplace 2.0. This risk is compounded by OIC’s operating with a streamlined Corporate Services group in which corporate knowledge of key organizational information, skills and expertise is retained by a limited number of individuals. | Office move is complete. As an Agent of Parliament, workforce turnover is a constant risk. |
| 4 | Change management | The risk that ongoing organizational changes across key functional areas, core processes and systems, combined with the physical move to a Workplace 2.0 environment in 2013–2014, will divert management focus and OIC resources away from their key function of ensuring efficient investigations and quality resolution of complaints. |
Office move is complete.
As legislative changes to the Act have been tabled, there could be future changes to the number of complaints and operations at the OIC. |
| 5 | Information technology (IT) and management (IM) security | The risk that the office relocation will present challenges related to meeting physical and IT-related policy requirements in light of vulnerabilities linked to shared areas and technology platforms that impact on the OIC’s ability to demonstrate exemplary practices and/or on its reputation. | Office move is complete. The impact of a security breach is considered very high and, therefore, this risk is perpetual. |
| 6 | Inadequate performance measures and targets | The risk that the performance measurement framework and/or data collection strategy will not support ongoing monitoring and reporting of key performance indicators, and the timely identification and implementation of required corrective measures. Also, the risk that performance targets do not reflect the OIC’s current inventory, the growing complexity of investigations, the anticipated increase in litigation cases, financial and human resources constraints, as well as the impact of ongoing organizational and policy changes. The inability to meet planned targets could affect OIC’s reputation. | The OIC has developed performance targets and goals for the investigators since the last RBAEP. These goals establish monthly targets for the number of complaints resolved per investigator and are monitored closely by senior management. |
Appendix B: OCG Prioritization of the Audit Universe – Small Department Risks
| Rank | Auditable Entry | Risk level | OCG Risks Identified |
|---|---|---|---|
| 1 | Information Technology Management | Very High |
|
| 2 | Compensation | Very High |
|
| 3 | Management of Shared and Common Services | Very High |
|
| 4 | Workforce Management | Very High |
|
| 5 | Security Management | Very High |
|
| 6 | Contracting and Procurement | High |
|
| 7 | Regulatory Management | High |
|
| 8 | Management and Oversight (financial and non-financial information for decision making) | High |
|
| 9 | Investment Planning and Project Management | High |
|
Appendix C: OIC Interview Results and Risk Evaluation
| Interviewee | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | Totals | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Risks | I | P | I | P | I | P | I | P | I | P | I | P | I | P | I | P | I | P | I | P | I | P | I | P | I | P | Total Score |
| Information Technology Management | 4 | 2 | 5 | 3 | 5 | 2 | 4 | 3 | 5 | 2 | 5 | 2 | 4 | 1 | 4 | 1 | 4.5 | 2.0 | 3.3 | ||||||||
| Compensation | 2 | 5 | 2 | 5 | 5 | 5 | 2 | 5 | 1 | 5 | 2 | 5 | 2 | 5 | 2 | 5 | 2 | 5 | 1 | 1 | 1 | 1 | 2.0 | 4.3 | 3.1 | ||
| Management of Shared and Common Services | 2 | 2 | 4 | 4 | 4 | 4 | 3 | 3 | 3 | 3 | 2 | 5 | 3 | 3 | 3 | 3 | 3 | 3 | 3.0 | 3.3 | 3.2 | ||||||
| Workforce Management | 3 | 2 | 3 | 4 | 3 | 3 | 3 | 4 | 3 | 3 | 4 | 4 | 3 | 4 | 5 | 5 | 2 | 2 | 4 | 3 | 3.3 | 3.4 | 3.3 | ||||
| Security Management | 1 | 1 | 4 | 2 | 3 | 3 | 5 | 3 | 2 | 2 | 4 | 3 | 4 | 3 | 3.3 | 2.4 | 2.9 | ||||||||||
| Contracting and Procurement | 4 | 4 | 4 | 2 | 3 | 5 | 2 | 2 | 3.3 | 3.3 | 3.3 | ||||||||||||||||
| Regulatory Management – Legislative Changes to Act | 4 | 4 | 5 | 2 | 5 | 2 | 5 | 2 | 4 | 3 | 5 | 5 | 5 | 5 | 2 | 5 | 3 | 5 | 4 | 3 | 4 | 3 | 4.2 | 3.5 | 3.9 | ||
| Management and Oversight (financial and non-financial information for decision making) | 3 | 3 | 4 | 2 | 4 | 2 | 3.5 | 2.2 | 2.8 | ||||||||||||||||||
| Investment Planning and Project Management | 3 | 3 | 4 | 4 | 1 | 1 | 1 | 2 | 1 | 2 | 1.9 | 2.3 | 2.1 | ||||||||||||||
| Changing complaints picture | 4 | 4 | 5 | 2 | 5 | 2 | 2 | 4 | 4.0 | 3.0 | 3.5 | ||||||||||||||||
| Change management | 1 | 1 | 4 | 4 | 1 | 1 | 2 | 4 | 3 | 3 | 3 | 3 | 2.3 | 2.7 | 2.5 | ||||||||||||
| Inadequate performance measures and targets | 1 | 1 | 1 | 1 | 1 | 2 | 1 | 1 | 1 | 1 | 1.0 | 1.2 | 1.1 |
- Eleven interviews were conducted in person and one over email
- Interviewees only ranked risks that applied to their area of expertise
- Risks were ranked from low (1) to high (5) for Impact (I) and Probability (P)
Appendix D: OIC Risk Heat Map
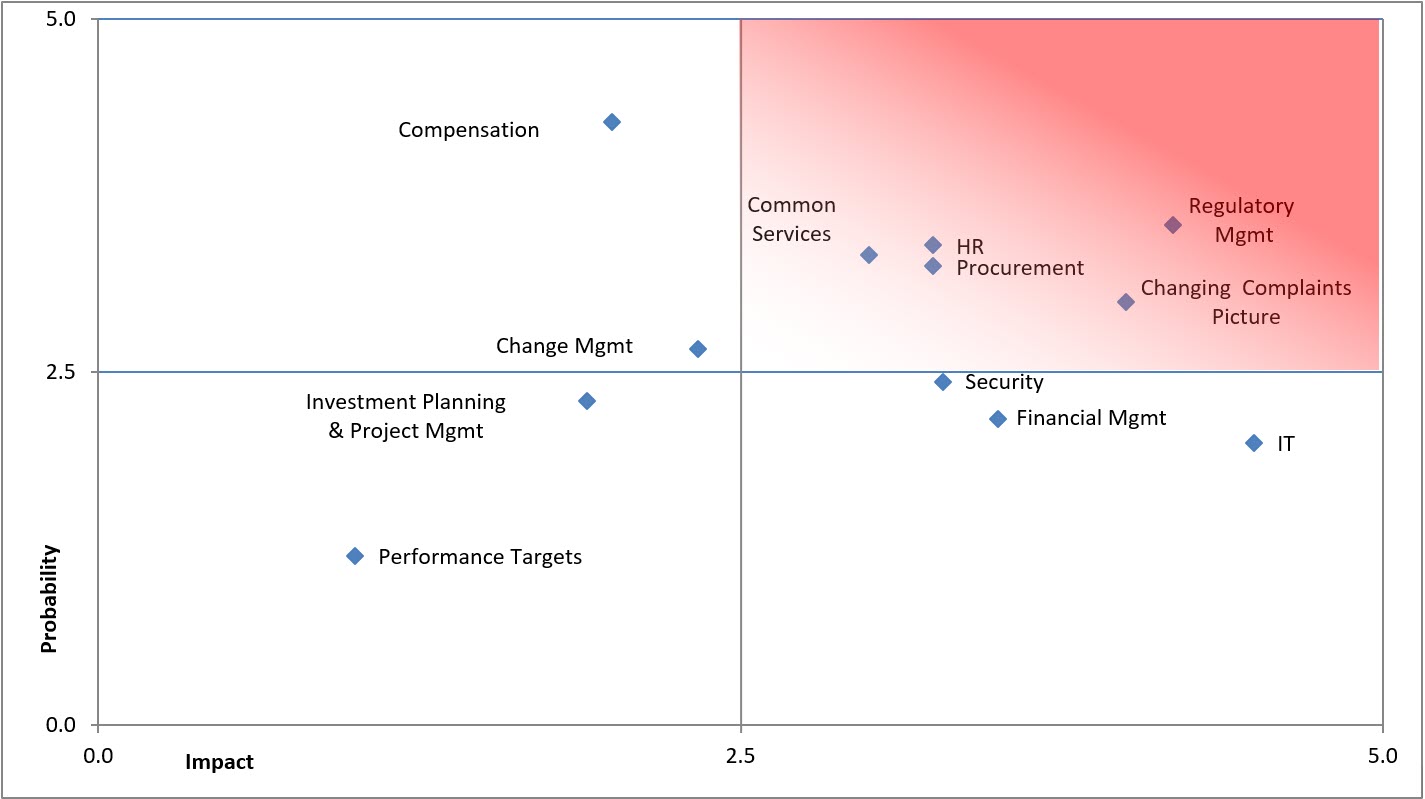
Text version
Potential risks were ranked from low (1) to high (5) for Impact (I) and Probability (P). The following were scored as follows:
For Information Technology, the score was 4.5 for Impact and 2.0 for Probability.
For Compensation, the score was 2.0 for Impact and 4.3 for Probability.
For Management of Shared and Common Services, the score was 3.0 for Impact and 3.3 for Probability.
For Workforce Management, the score was 3.3 for Impact and 3.4 for Probability.
For Security Management, the score was 3.3 for Impact and 2.4 for Probability.
For Contracting and Procurement, the score was 3.3 for Impact and 3.3 for Probability.
For Regulatory Management, the score was 4.2 for Impact and 3.5 for Probability.
For Management and Oversight, the score was 3.5 for Impact and 2.2 for Probability.
For Investment Planning and Project Management, the score was 1.9 for Impact and 2.3 for Probability.
For Changing complaints picture, the score was 4.0 for Impact and 3.0 for Probability.
For Change management, the score was 2.3 for Impact and 2.7 for Probability.
For Inadequate performance measures and targets, the score was 1.0 for Impact and 1.2 for Probability.
Appendix E: Organization Chart
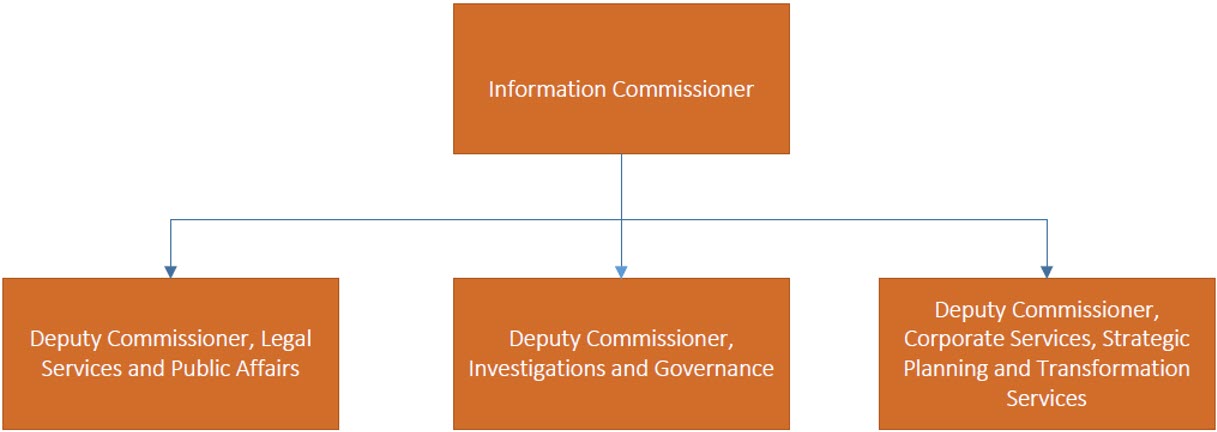
Text version
This hierarchal chart shows the organizational chart at the Office of the Information Commissioner. The Information Commissioner is at the top of the hierarchy as the head of the organization. On the second level, there are three Deputy Commissioners. On the left, is the Deputy Commissioner of Legal Services and Public Affairs. In the middle is the Deputy Commissioner of Investigations and Governance and on the right is the Deputy Commissioner Corporate Services, Strategic Planning and Transformation Services.